Access Control
CyberLock®
CyberLock electronic cylinders replace standard mechanical cylinders.
Each CyberLock cylinder is an electronic version of a standard mechanical lock cylinder. Installing the cylinder into the lock hardware is as simple as removing the existing mechanical cylinder and replacing it with the CyberLock cylinder.
No wiring or battery is required at the lock.

The lock installs without wiring of any kind, and does not contain a battery. The power required to open a lock comes from the battery in the key. To incorporate hard-wired doors please see our Flex System.
Cylinders cannot be picked.
CyberLock cylinders have no through hole, therefore they cannot be picked like a mechanical lock. The cylinders can resist forced rotation and are designed to remain in the locked position if tampered with.

CyberKey®
CyberKey electronic keys use a 3-volt lithium battery, easily replaceable in the field, or can be recharged depending on the model of key.
Keys cannot be duplicated.
It is not possible to create a duplicate of a CyberKey smart key. Passwords in the software and hardware are unique to each installation, and protect against creation of unauthorized keys. And, although two keys in the system can be programmed alike, each one will make its own unique record of events in the software.
-
Each key contains a list of locks it can open, with days and times.
The CyberKey smart keys are programmed with the access privileges for each user. A standard key holds a list of locks the user can open, with the schedule of days and times they are allowed in.
-
Keys can be assigned a begin date and an expiration date.
This means keys can be issued before they begin working and can be set to expire at a particular time in the future. Setting short-term expiration dates on keys is an excellent way to minimize risk due to lost or misplaced keys.
-
One key can be programmed to open doorways, padlocks, cabinets, safes, ATM machines, and more!
Data Transfer
A record of all events is stored in both the locks and the keys.
Each time a key is used at a lock a record of the lock ID, date, and time is stored in the key; and a record of the key ID, date, and time is stored in the lock. The key stores up to 3,900 of the most recent events and the lock stores the most recent 1100 events. Locks and keys can also record when an unauthorized person attempted to open the lock.
CyberVault
Entry On Demand
The CyberVault key vault enhances the CyberLock system by providing the ability to allow people access to specific areas without the need for them to have their own key.

20-Key Vaults add two primary benefits to a standard CyberLock system:
- The ability to have "shared keys" while having individual access privileges and tracking.
- Keys are held in a disabled state until needed. If a key is removed it will not open a lock.
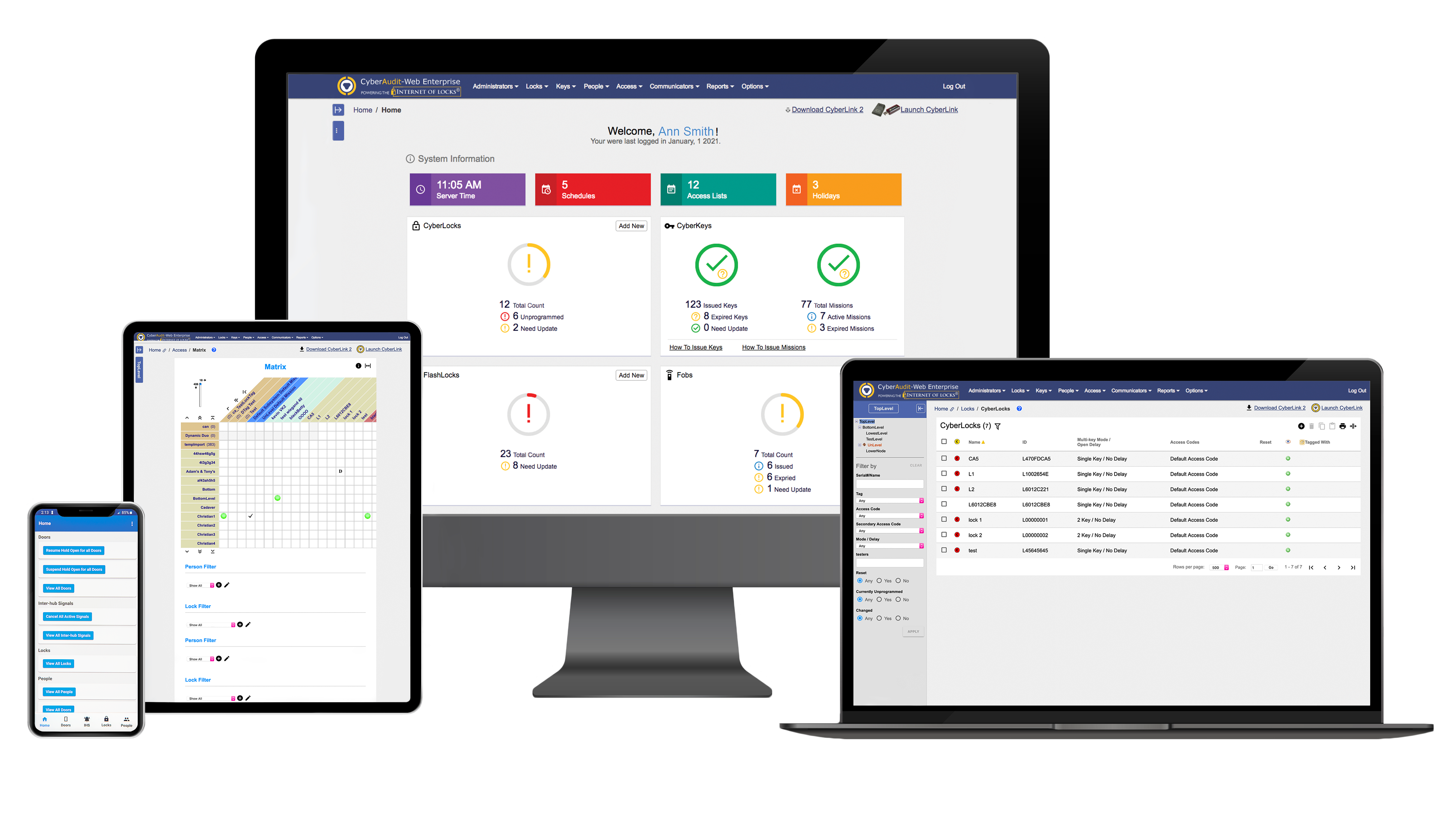
CyberAudit-Web Software Options
-
CyberAudit-Web Enterprise
CyberAudit-Web Enterprise is a comprehensive, feature-rich software ideal for large, widespread businesses and campus settings. The Enterprise system is specifically designed for installations of over 1,500 locks, keys, and 500 concurrent users with the need for in-field changes.
Enterprise users can easily access the software from any computer on a local network or just by opening a web browser and logging on. In addition to all of Professional's features, a hierarchy of administrators can also be set, allowing each manager in the organization control over only the locks, keys, and people in their area of responsibility.
NARCOTIC TRACKING SYSTEM (NTS)
The NTS is designed to monitor your narcotics from storage to go-bag to ambulance and then back to storage.
The NTS is outfitted with our high-security CyberLock Access Control System. Locks cannot be picked, keys cannot be duplicated. The CyberAudit software can grant or restrict individual permissions to specific locks.
Each time a key is used, a record of that event is stored in both the lock and the key. Access granted and access denied events are both recorded.
-
Stage One
Storage/Removal
For installations that return narcotics to storage after their shift, we have 8 & 16-door lockers with master doors. Now you can track when the narcotics were added and removed for transport.
-
Stage Two
Transport
Our small box (EAW-NTSSB) is designed to be lightweight and secure. You can go from storage to the field without adding extra weight to your packs.
-
Stage Three
On-Board Storage
Our large box (EAW-NTSLB) is designed to be secured on the truck. The small box fits inside with room left for anything else that needs to be secure.
All boxes have ventilation for temperature control.
FLEX SYSTEM
Flex System Integrated Security Solutions
The CyberLock Flex System is a modular integrated security solution that combines all the benefits of a wired door security solution with the CyberLock key-centric, non-wired, access control solution and all managed under one unified software platform.

-
Flexible
The heart of the system is built around the Flex System Hub access controller which provides connections for, and power to, weatherized modules that can be mixed and matched to fit your access control needs.
-
Expandable
A wide variety of other security devices such as HID readers, request-to-exit devices, alarms, door sensors, and more can be added to the Flex System through the Door Controller & I/O module.
-
Compatible
The Flex System is managed by CyberAudit management software, the same platform behind the award-winning CyberLock access control system composed of electronic lock cylinders and programmable smart keys.
“CYBERKEY®, CYBERLOCK®, and CYBERAUDIT® are registered trademarks of Videx, Inc. in the United States and other countries.”